(7 min read)
This blog is a little longer than normal, but something got me started!
Many companies engage in fake phishing campaigns – an exercise where employees are deliberately sent emails that are designed to see whether the employee will open the email, click on a link or open an attachment.
These are often part of a cyber-training programme, and they are often completely counterproductive. Psybersafe founder, Mark Brown, considers whether these campaigns are useful or not.
A recent article in the Wall Street Journal: Why Companies Shouldn’t Try to Catch Employees With Fake Phishing Emails, raised some interesting points. In the article, the author suggests that phishing simulations or campaigns in organisations create stress and distrust among employees—without significantly improving the organisation’s defences. "While early research suggested that phishing simulations could reduce click rates on subsequent fake phishing emails by about 50%, more recent studies in more realistic settings and with larger groups found little to no improvement in click rates after mock campaigns were conducted.”

Success depends on context
We know that for any phishing attempt, or other social engineering attempt, context is the trump card. Yes, it’s important to be alert to unexpected emails, poor grammar and the ‘obvious’ features of a phishing attempt. But, a bad, obvious phishing mail will still get clicked if the email is particularly relevant to the reader’s situation at the time. And psychology can explain why.
One of the examples in the article is a case where employees received a phishing mail suggesting they could get more email storage. More employees clicked on it because it happened to be sent around the same time the company was actually upgrading email accounts.
In my own experience of conducting phishing campaigns during the COVID pandemic, COVID-related emails received far more clicks as this was the big news at the time, affecting pretty much everyone. But an email offering a spa voucher to employees of an engineering firm, using their work email address, for example, is contextually odd and much less likely to be clicked on. The message and its context are key.
Don’t trick your employees

If you’re going to conduct a phishing campaign, you need to do it appropriate to the culture of your organisation. Whether employees feel tricked and cheated depends entirely on how the campaign is conducted, explained and used. Set out to trick and punish and you will get negative reactions. On the other hand, position it as helpful, supportive and useful and you can elicit goodwill and increase awareness.
In my experience, phishing campaigns alone do not work. Employees need both the awareness and the tools to protect themselves and the organisation. Therefore, only a comprehensive training programme will have any lasting and measurable effect.
This training can be both affordable and non-disruptive to your organisation. We know from developing the unique Psybersafe online training programme that the right techniques from psychology and behavioural science can create friendly, useful and very effective security knowledge, attitudes and behaviour.
Why are phishing campaigns so popular?
Because they give you hard data: the number of emails sent, the number clicked on, the number reported and so on. But the data is often misinterpreted – largely because you can’t always tell who’s opened the email, and because click rates are often red herrings.
People will get caught out - we have to recognise that we humans will make mistakes - most often inadvertently. So, the emphasis should be not on whether the employee made the mistake, but whether they knew what to do once they realised they had done something wrong.
If someone clicks your phishing email but does not report it, you need to understand why not – it may not be because of wilful neglect or ignorance. For example, if the email is set up so that the click takes the employee to a message that says: ‘You clicked on a phishing mail’ and gives an explanation or some kind of advice or education, people may not feel the need to report further. And, of course, if you don’t have a clear reporting process in place, do your employees even know how to do it?
Is it wrong to use fear to prompt action?
Psychology research suggests that if you use fear, you must give people a way to tackle that fear. If you scare me, and I cannot do anything about it, it will cause mental discomfort – and cognitive dissonance. Without guidance, my online option is to ignore or bury the feelings.
It’s my view that it’s OK to use fear, in the right way, as long as you give people ways to take action to tackle that fear and protect themselves.

For example, by using a password manager to save complicated long passwords, or use a VPN to avoid getting attacked via public Wi-Fi. So a good phishing campaign must have the right context, be communicated in the right way and deliver a prompt and useful learning experience that genuinely helps people to tackle the problem.
Phishing campaigns alone don’t work
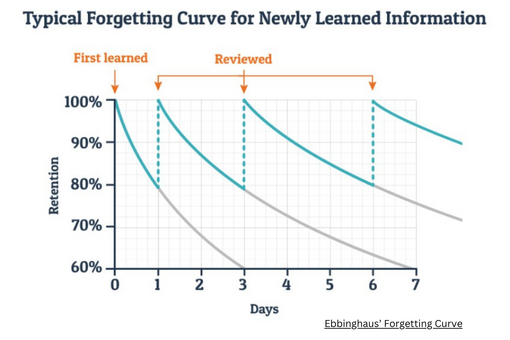
Cyber security training needs to be done far more often than once, twice or even four times a year. When we look at the ‘human factor’ in cyber security, we can see that a few seminars a year will not change anyone’s routines or habits. You only have to look at Ebbinghaus’ Forgetting Curve, which shows that you’ll forget what you saw in that seminar very quickly - 50% within an hour and 80% within a month.
Plus, the adult attention span is typically less than 10 minutes. And when you’re talking about a subject that does not feel particularly important to you, and you’re busy and time-poor anyway, the impact is likely to be minimal. To make matters more difficult, long-ingrained habits and routines are not easy to shift and replace with better behaviours.
That’s why, in order for cyber security training to really succeed in changing the way your people behave, you need ongoing training that’s reinforced with exercises and reminders. It doesn’t have to take long, or cost the earth – it just has to have a behavioural science basis, a fun interface and proven results.
If you’d like to see how Psybersafe can do better than a random fake phishing campaign, why not contact us today?
Sign up to get our monthly newsletter, packed with hints and tips on how to stay cyber safe.
 Mark Brown is a behavioural science expert with significant experience in inspiring organisational and culture change that lasts. If you’d like to chat about using Psybersafe in your business to help to stay cyber secure, contact Mark today.
Mark Brown is a behavioural science expert with significant experience in inspiring organisational and culture change that lasts. If you’d like to chat about using Psybersafe in your business to help to stay cyber secure, contact Mark today.